If you keep up with cybersecurity news, you are probably aware that the cost and occurrence of data breaches continue to rise. Organizations are under continual attack, and the transition to remote labor is intensifying the issue.

We'll talk about network segmentation in this post, covering what it is, why it's essential, and the advantages of executing a solid network segmentation plan.
Network segmentation is an architectural technique for dividing a network into many parts or subnets, each of which functions as its own separate network. This allows network managers to use granular policies to govern traffic flow between subnets. Segmentation is used by businesses to increase monitoring, performance, pinpoint technical faults, and, most critically, improve security.
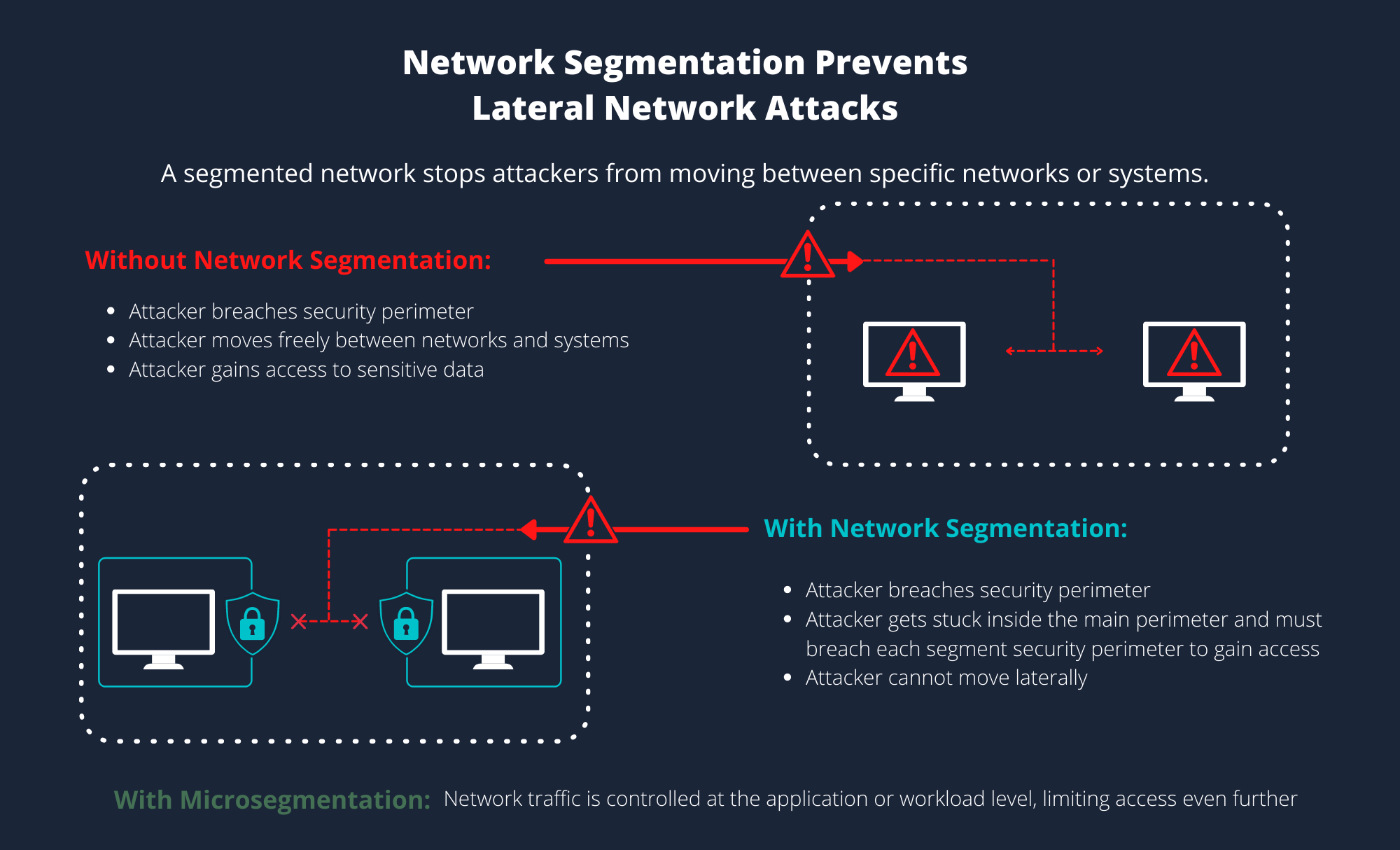
Network segmentation successfully prevents a single point of failure and makes it impossible for unauthorized users to jeopardize the whole network by isolating (or segmenting) the network into discrete contained pieces.
If a bad actor acquires access to your network, for instance, they will attempt to navigate the network in order to gain access and use sensitive data. It is relatively easy for a bad actor to gain access to the entire system through one access point if you have a flat network (an architecture in which all systems are connected without going through intermediary devices such as a bridge or router). While flat networks enable quick and dependable communication, its lateral access across systems makes them particularly susceptible in today's contemporary, networked businesses.
Malicious traffic, on the other hand, will not have rapid access to the entire ecosystem if the network is divided. Attackers will only be able to access the first area of the system they broke, allowing IT time to find the breach and mitigate the harm.
Network Segmentation Benefits
Enhanced Monitoring. Allows for the logging of events, the monitoring of approved and forbidden internal connections, and the detection of suspect activity.
Enhanced Performance. Local traffic is reduced when there are fewer hosts per subnet. Broadcast traffic can be restricted to a single subnet.
Enhanced Security. To limit and/or prevent access between network parts, network traffic can be separated and/or filtered.
Improved Containment. When a network problem occurs, its impact is restricted to the local subnet.
Improved Access Control. Allow users to access just particular network resources.
How network segmentation may help you meet zero trust and compliance requirements
You have possibly heard of zero trust, a prominent network security concept that solves the cybersecurity challenges that most businesses face today. Nothing, even users or programs currently inside the network perimeter, should be trusted by default in a zero trust environment.
Before network access is given, all users, devices, and endpoints must pass verification. By default, unverified connections are rejected, whereas authorized connections are subject to a stringent policy for the life of their network access.
While network segmentation is a concept and a method, it symbolizes a larger movement in cybersecurity philosophy toward the zero-trust paradigm. You're adopting the "trust no one" mentality by segmenting network routes.
Still, in terms of zero trust, network segmentation is insufficient. Network segmentation is regarded as north-south traffic control, which means that any users, applications, or devices authenticating into a specific network zone of the network are trusted. More constraints are necessary if someone is authenticated to access an entire segment purely based on physical or logical location, rather than identity. This trust paradigm can lead to security vulnerabilities, necessitating the use of micro segmentation.
Planning and Execution Strategies for Network Segmentation
Although the benefits of segmenting a network to discover and address security gaps are highlighted in best practices for network segmentation, adopting network segmentation may sometimes be unfavorable. To prevent both over and under segmentation, it's critical to build your strategy around clear rules that you can follow to get the best outcomes.
Clear vision - Before starting to segment the network right away, it's a good idea to assess the existing state of the company's security and create a picture of what needs to be done to enhance it. Network segmentation may be accomplished in a variety of ways. Identifying current gaps and aligning with the best solution necessitates answering the following questions:
What are the advantages of deploying network segmentation for our company?
Why do we think it's a good strategy for our business?
At what point should segmentation begin to yield real results?
What effect will it have on the company's operations and results?
What aspects of the project should be examined and improved?
Revision of current security framework - There is no need to rewrite a security environment that is already functional. The key aim of network segmentation is to upscale current processes and policies so that protection is smoothly raised to an advanced level — not only to destroy working patterns and rebuild them with a comparable outcome just for the pleasure of doing so. To make it work for the firm, it's a good idea to audit the existing network, see what security features are already in place, and emphasize what's working and what needs to be enhanced.
Create your own action roadmap - In order to become a more agile firm, you must also consider the implementation process. By breaking down the network segmentation implementation plan into smaller chunks, you may spot any areas where you can enhance or make a minor strategy modification along the road.
Examine resources and capabilities - An internal audit of an organization's network, as well as internal information resources, are useful in determining the scope of the project. Categorization is essential for determining which components may be grouped together and which specific requirements they must meet in order to function together under specified security standards. What is the extent of network traffic, can it be fragmented, and what effect will re-structurization have on network limiting performance?
After you've completed your preparations, it's always a good idea to establish a healthy working culture by agreeing on activities and documenting the process. Once there is no beta version for the project, there is no way to start the process — testing network segmentation implementation is a critical aspect of creating a seamless transition to a safer network environment.
Poor resource management, for example, is one of the most important factors that may and should be considered as fundamental problems. Staff capabilities, available people and their skill sets, current budget, and expected and unforeseen costs, are all covered by resources.
Barriers to Network Segmentation - Cohesive planning and preparation work prior to the actual implementation aid project managers in anticipating any issues that may arise during the deployment. Some of the obstacles, on the other hand, can be overcome before they become a problem later in the process.
Overcoming Obstacles - As part of a general, in-depth prospecting of network segmentation practices, becoming familiar with potential challenges and mapping out efficient solutions is critical for achieving proper traffic control to provide access to separate zones on a network and improve security against a successful breach.
Lack of "airbags" in the process - Even the most meticulous preparation can occasionally result in the failed implementation of new processes and work frames. To avoid fallbacks, strong time management and leadership support are required to return to implementing network segmentation policy, which, among other things, reduces the cyber attack surface, helps regulate local traffic, and permits third-party access restriction.
The vision isn't crystallized - A broad roadmap with stated "ifs" enables a smooth transition to network segmentation. Identifying planning flaws and maintenance requirements early on increases the chances of avoiding human mistake.
After determining whatever security measures are currently in place and making strategic judgments based on the benefits and drawbacks, it is preferable to pick software-defined networking from the market's well-adaptive, simply expandable, and simple-to-install solutions for efficient deployment. They can also help fill up security holes despite having limited information, staff, time, and funding resources. Better access to a corporate network and endpoint security via network segmentation best practices will be raised in no time if any incoming red signals are dealt with care and maintaining a dynamic mentality is a focus.
Your network is under constant monitoring with Annexus Technologies, and our team of cybersecurity professionals is always hunting out dangers in the huge cyber cosmos. Within minutes after an attack, incidents are discovered and confirmed for you, and remedial advice are sent.
