Data Security: Top Threats and Best Practices

With the digital world continually evolving, cyber security is one of the fastest-growing sectors. More individuals than ever before are becoming aware of the necessity of data protection and of cyber security concerns. Everything you need to know about data security for your business will be provided here, including the most common threats, regulatory requirements, and best practices.
What Is the Importance of Data Security?
Data security is important since a data breach can have major consequences for your company. This primarily means money – according to IBM and The Ponemon Institute, the average data breach in 2020 costed $3.86 million:
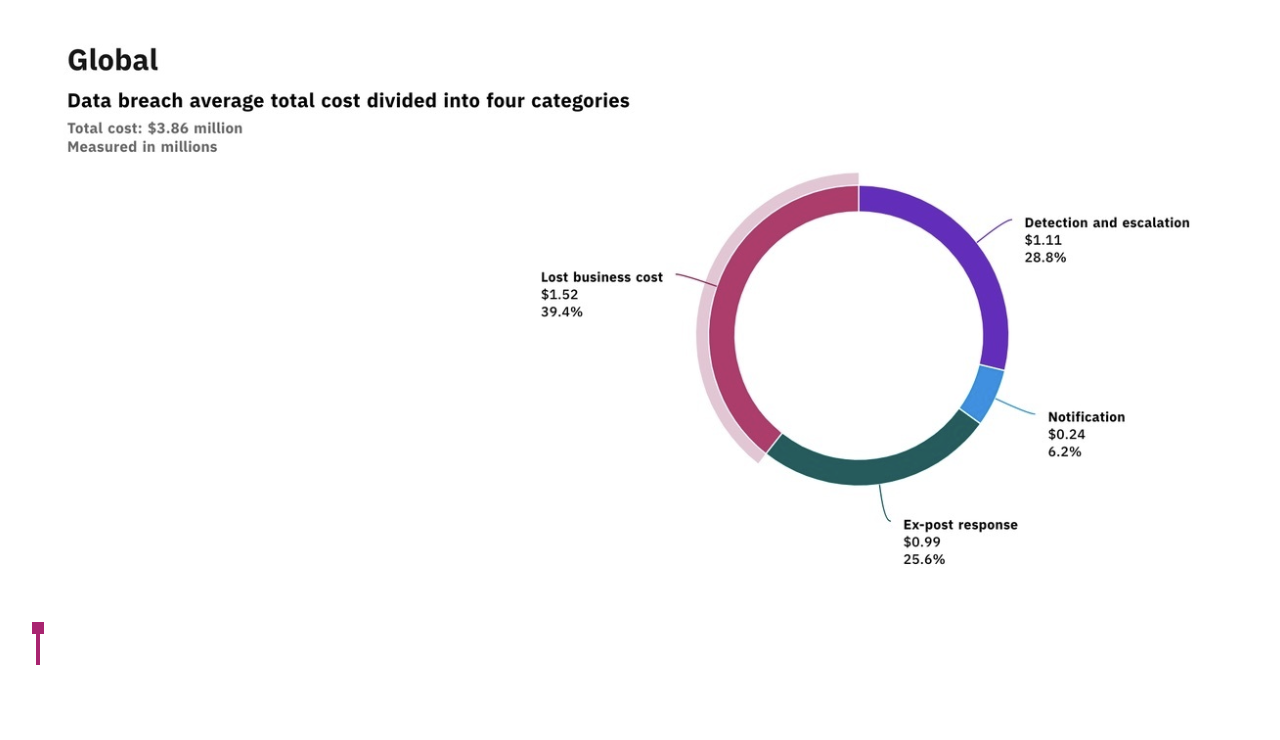
Courtesy of IBM/Ponemon Institute
The loss of business that follows a data breach accounts for most of the direct expenses connected with it. Nevertheless, 71 percent of CMOs feel that the most significant impact of a data breach is on brand equity and value.
As reported by Interbrand, a brand valuation firm, "the role the brand plays in purchase decisions." accounts for a significant portion of a brand's worth. To put it another way, having a strong brand can increase your clients' willingness to pay for your products or services.
Poor brand equity, on the other hand, might have the opposite impact. And, given that studies show that 65 percent to 80 percent of customers would lose faith in a firm that has exposed personal data (a big blow to brand equity), the potential consequence of a data breach might have a long-term impact on your brand.
Data Protection vs. Data Security vs. Data Privacy
Because they all pertain to techniques to secure your data, data security is sometimes confused with phrases like "data protection" and "data privacy." The distinction between these phrases, however, is found in the motivations for safeguarding data in the first place, as well as the means used to do so:
Data protection is the process of creating backups or duplicating data in order to safeguard it against inadvertent deletion or loss. A good example of data protection is making a backup of your data so that if it becomes damaged (or if your servers are destroyed by a natural disaster), you won't lose it permanently.
Data security refers to safeguarding your information from unauthorized access or usage that might expose, delete, or corrupt it. Using encryption to prevent hackers from accessing your data in the case of a breach is an example of data security.
Data privacy relates to issues about how your personal information is treated, such as regulatory concerns, notification, and consent to use, among other things. Obtaining approval to gather data from website visitors via cookies is an example of data privacy.
Regulations and Compliance with Data Security
The majority of nations have stringent data security standards that businesses must adhere to. Violations of these rules might result in significant fines. Usually, regulatory compliance is difficult to negotiate, as standards differ between countries (or regions in certain countries, such as the United States) and depend on the type of data that is being processed. One of the finest things you can do is make sure you have competent legal counsel on hand to assist you with your legal needs. Nevertheless, the following are some of the most essential and far-reaching data governance rules that may have an impact on your company.
General Data Protection Regulation (GDPR)
The GDPR is the European Union's data protection and privacy regulation. It was approved in 2016 with the goal of protecting consumers and unifying data management standards for local and foreign enterprises. Any entity that handles personal data must take "appropriate technical and organizational measures" to secure such data (together with obtaining an individual's agreement to store and use it), according to the GDPR. This entails obtaining users' consent to gather their data, anonymizing that data to safeguard users in the case of a data breach, and adhering to certain criteria for alerting users in the event of a data breach.
Health Insurance Portability and Accountability Act (HIPAA)
HIPAA is a federal statute that governs the security and protection of digitally protected health information in the United States (ePHI). It was enacted in 1996 to regulate and modernize the individual health data management, including fraud and theft protection rules, how insurance companies may and cannot use it to bill individuals for services, and more. Any organization that processes ePHI must follow HIPAA's technological, physical, and administrative precautions. Violations can result in fines of up to $250K and up to ten years in prison.
Sarbanes-Oxley Act (SOX)
In 2002, the Sarbanes-Oxley Act was enacted to further safeguard company investors from financial fraud. It was meant to enhance the penalty for erroneous or inadequate financial reporting in response to a series of high-profile corporate accounting crises (such as Enron) (including manipulating financial data to present it a certain way). It also provides rules for controlling access to business financial data. SOX primarily affects public companies and the manner they report financial data. However, some parts apply to private businesses as well, such as manipulating financial records or retaliating against workers who disclose financial crimes.
Federal Information Security Management Act (FISMA)
FISMA was enacted in 2002 to standardize the way federal agencies in the United States handle data. It mandates that all government agencies (as well as private-sector subcontractors and service providers) adhere to strong information security rules (FIPS 200) and auditing processes to assure compliance.
The Most Dangerous Data Security Threats

Here are 10 of the most serious cyber security concerns that businesses face today.
10. Cryptojacking
Cryptojacking is a sort of cybercrime in which hackers utilize people's gadgets (cellphones, computers, tablets, and even servers) to mine crypto without their permission. The aim is profit, like with many types of cybercrime, but unlike other dangers, it is meant to remain fully concealed from the victim. Because crypto mining necessitates massive quantities of computer processing power, hackers gain money by discreetly piggybacking on other people's workstations. Cryptojacked systems generate major performance concerns for organizations, as well as costly downtime as IT teams have to trace down and remove cryptojacking programs.
9. Phishing attacks
In the digital threat environment, phishing attacks continue to play a significant role. In 2021 Data Breach Investigations Report (DBIR), Verizon Enterprise discovered that phishing was one of the most common types of data breach activity. Phishing was found in more than a third (36%) of the breaches, according to the researchers. This is a significant increase from 22% a year ago.
8. Endpoint Security
The attack surface grows as more firms shift resources to the cloud and rely on remote workstations. The difficulty for businesses is figuring out how to keep these off-premise systems and personal devices safe. Cybercriminals routinely utilize endpoint assaults to gain access to bigger networks. Enterprises keep more control over cyber threats and efforts by requiring endpoint devices to fulfil security requirements before being permitted network access.
7. Exposure to a Third-Party
Even with the same vendor, various connections expose an organization to varied levels of risk. Many merchants outsource services like payment processing to third parties. Even if a corporation does not handle personal data directly, such as social security numbers or credit card numbers, a third party can compromise them. Hackers can steal data from third-party businesses via malware.
6. Internet of Things (IoT)
IoT uses the internet to link gadgets from all around the world. Sensors collect, communicate, analyse, and act on information in the IoT, according to Deloitte, providing new ways for media, technology, and telecommunications businesses to create value, whether that means creating entirely new businesses and revenue streams or providing a more efficient experience for consumers. Many individuals and businesses are taking advantage of IoT because it is easy, but the exact feature that makes it handy also makes it susceptible. Hackers can use internet connectivity as a point of entry to steal information. Many experts believe that as firms increasingly rely on IoT devices, this will be one of the most serious security dangers in the future years. According to a Fortune Business analysis, the IoT industry is expected to reach $1.1 trillion by 2026.
5. Formjacking
Formjacking is a sort of cyberattack in which hackers insert malicious JavaScript code into a web form–usually a payment page form. When a site user inputs their credit card information and clicks submit, malicious code grabs the card number as well as additional information such as the customer's name, address, and phone number. The malware then delivers this data to the attackers' preferred destination. Cybercriminals frequently use eCommerce sites' checkout pages to steal financial information and credit card details. The idea is to scan through the forms for important information. According to Symantec's Internet Security Threat Report, formjacking has expanded considerably. Each month, an average of 4,800 websites are infected with formjacking malware, according to the research.
4. Patch management
Many cyber-attacks begin with out-of-date software. Companies that do not keep up with software patches are subject to data security breaches, and as soon as attackers discover a software weakness, they may use it to begin a cyber-attack. The process of delivering and installing software updates is called patch management. These patches are frequently required to address software errors (also known as "vulnerabilities" or "bugs").
3. Cloud security flaws
The greater our reliance on the cloud for data storage, the greater is the possibility of a massive security compromise. Although cloud services are vulnerable to a variety of attacks, many firms assume they are safe because they employ cloud security technologies. Technology, in actuality, is only a part of the answer. Because no technology can totally remove vulnerabilities, comprehensive protection is required. As part of a complete cyber risk management plan, insurance is a crucial component of that protection.
2. Social engineering
Social engineering attacks take advantage of social interactions to get access to sensitive information. Cyber thieves use deception and manipulation to persuade their victims to take certain activities, such as circumventing security measures or releasing sensitive information. Since the target lets the hacker inside the system, even the strongest cyber security systems can't stop a social engineering attack.
1. Attacks by ransomware
Ransomware is a sort of software that restricts you from using your computer or accessing the information saved on it. The data on the computer may be deleted, stolen or encrypted, or the machine itself could be locked. The attacker will then demand a ransom from the victim in exchange for restoring access to the data.
According to Check Point's mid-year security report, ransomware assaults have escalated considerably over the last year, with 93 percent more carried out in the first half of 2021 than the same period last year. In only the first six months of this year, there was an estimated $590 million in suspicious activity tied to ransomware assaults, according to a US Treasury Department analysis. That sum was only $410 million for the entire year of 2020.
Types of Data Security Technologies
You may protect your data using a number of different technologies. To ensure that all potential entry points are secured, you'll want to use as many as possible.
Encryption
Data encryption uses an algorithm to scramble sensitive information, making it impossible to read without the exact knowledge (the encryption key) needed to decode it. It's a critical data security technique since it assures that even if someone acquires illegal access to your data, they can't utilize it. You should always make sure that your encryption keys are kept safe and that only a few people have access to them.
Authentication
Authentication is the process of confirming a user's login credentials (biometrics, passwords, etc.) to ensure that they are who they say they are. It's also one of the most crucial components of your data security plan since it acts as a first line of protection against unwanted access to sensitive data. Authentication is conceptually easy, yet it is extremely challenging to do right at scale in terms of technology. New technologies such as multi-factor authentication (MFA), single sign on (SSO), and compromised password detection, on the other hand, are making it simpler than ever to secure login without degrading the user experience.
Tokenization
Tokenization is a process that is comparable to encryption. Tokenization, on the other hand, replaces your data with random characters rather than scrambling it using an algorithm. The link to the original data (the "token") is then saved in a different database table that is password-protected.
Physical Access Controls
Data access control is also a crucial component of any data security plan. Actual access control maintains access to the physical places where your data lives, whereas digital access control is frequently handled through authentication methods (and restricting the number of authorized users who have access to your data, your on-premises server rooms or a data center). Protective measures such as biometric authentication methods like fingerprint recognition and retinal scans, key cards, and security staff are all examples of physical access management controls.
Data Masking
Data masking is performed by "masking" your data's characters with proxy characters rather than transforming data into an intermediate form. Once it reaches its final destination, software reverses the process.
Ensuring Data Security: Best Practices
There are a lot of moving elements in a complete data security plan, all of which must operate simultaneously in real time to keep your data safe. The size and structure of your organization's computing infrastructure will determine how your plan is implemented. Therefore, what follows isn't a step-by-step description of everything you need to do to achieve flawless data security; rather, it's a high-level review of the key principles that come together to provide a solid data security foundation.
Keep your data safe
Securing your data where it's stored is an important aspect of data security. We will present three suggested practices for strengthening the security of your data storage locations:
Protect user data at the point of origin. When consumers and workers log in for the first time (or again), you may use safe authentication techniques like social login to validate and secure their information. This not only streamlines the process and lowers the risk of churn, but it also allows them to consolidate all their sensitive data in one place rather than in many databases and spreadsheets that are easily lost.
Control who has access to sensitive data. Controlling who has access to your data based on their user ID is a wonderful method to keep sensitive data accessible only to those who need it. This reduces the amount of harm that may be done if a user's username or password is compromised.
Everything should be encrypted. Encryption is one of the most effective technologies for keeping data secure. It assists you in ensuring that any information obtained by hackers is not used by them. To add an additional layer of security to any information you submit, make sure to encrypt transmissions.
Conduct Audits of Compliance
There are several guidelines that might assist you reduce the chances of a data breach. There are a few laws that you're likely compelled to observe that will assist you in doing the same thing. The rules that are relevant for your business can vary greatly depending on your sector and area, so you'll need to do some research to figure out which ones apply to you. However, if you process personally identifiable information, it's in your best interest to do a self-audit and ensure that your company is compliant. This will not only keep you out of legal issues, but it will also dramatically increase the security of your data.
Prepare For Threats
Because hackers are continually hunting for holes in your security systems, cybersecurity threats are always expanding and changing. As a result, data security isn't something you do once and forget about, it is something you do every day.
Here are the best strategies to prepare for future attacks (and the fallout from any breach):
Educate your workers. Employees who are uninformed of the hazards and have let their guard down are the targets of common data security assaults like spear-phishing emails and USB traps. Regularly disseminating common suggestions like those from Proofpoint or adopting Inspired eLearning's executive training can help mitigate these hazards.
Put your system(s) to the test. The greatest defense is a solid offense, and in safe data recovery, the best offense is primarily trying to avoid losing your data. However, while automation might assist you in monitoring your systems, it can’t match the ingenuity of a human attempting to get in. As a result, it's preferable to either form an internal team to stress-test your systems or hire someone to do it for you from outside the organization.
Make a safe data recovery strategy. It's crucial to be prepared to cope with corruption or the unfortunate event where something you need has been erased or corrupted. For many teams, this entails keeping a regularly updated backup copy of vital data. The backup should be password-protected and kept separate from the rest of your data.
Have a plan in place for dealing with incidents. Having a robust response strategy in place in the event that your data is compromised may greatly reduce the effect on your business. IT should be informed of what to do, but you should also develop standards for management, including notifying staff and recovery processes.
Delete any data that is no longer needed
Your data will become obsolete or no longer be useful at some point. When this happens, it's crucial to delete the data since it might still hurt your users if it's breached.
Because 65 percent of consumers reuse their passwords across many sites, an old password might still be used to hack their data at another organization if they haven't updated it on all digital accounts.
Two excellent techniques for removing unnecessary data are as follows:
Don't forget about physical copies as well. Don't forget about any backups that are on paper, saved on a USB drive, microfilm, negatives, or X-rays— or anything else that's physical and independent from your digital systems. Make sure that part of your procedure for eliminating useless data includes double-checking to determine if the data has a physical equivalent and, if so, destroying it in kind.
Understand when and how to let go. When it's time to get rid of digital data, be sure you do it correctly. You shred sensitive information on paper when you need to get rid of it. Before throwing away your credit cards, you break them up and write "VOID" on checks. Digital data is no exception. Make sure the information you're erasing is truly gone and not remaining anywhere that may come back to haunt you.
Don't Forget About Mobile Data Protection
According to McAfee's 2020 Q1 Mobile Threat Report, mobile assaults reached 150 million in the first half of 2018 and rose another 30% in 2019. Mobile security is becoming an ever more important aspect of your data security strategy as mobile hacks grow more common.
There are various things you may do to improve the security of your mobile data:
Delete any programs that are no longer in use. (A security breach may have caused providers to stop or eliminate access to them.)
Access to internal tools should need multi-factor authentication.
Update all applications on a regular basis to be safe against spyware.
For each new mobile account, create a unique password. Standard logins should never be used.
Check the list of permissions requested before installing new apps. If they appear to be excessively intrusive, employees should avoid downloading them since they may contain mobile malware.
Ensure that staff understands how to use their devices from afar. It's vital to be able to erase or move data quickly if a device is lost or stolen.
To limit access, use communication applications that encrypt data transmissions.
Keep in mind that mobile data security is not limited to smartphones and tablets. Other mobile devices, such as smartwatches and other wearable technologies, as well as video conferencing and other business productivity tools, are now also included.
Humans are responsible for data security.
More than ever, your workers are the first line of defense for the protection of your data. As a result, promoting the proper behaviors is critical to preventing a data breach at your company.
One of the most effective methods to do so is to improve your team's user experience. It is considerably simpler for users to follow cybersecurity best practices, such as using unique passwords for each application or using longer, more complicated passwords (which are harder to crack), when the user experience is simplified.
Building a simplified authentication experience for your whole organization is simple with Annexus Technologies. Here's where you can learn more about us.
